Security Research Archives
>
File Explorer
▼~/blog
▼categories
▶web-security(0)
▶red-team(1)
▶malware
▶recon(1)
▶binary-exploitation(0)
▶offensive-programming(0)
▶phishing(0)
▶mobile
▶misc(1)
▶talks(0)
▶tags
▶security-levels
▶status
▶README.md
$ find
Found 4 results
Found 4 results
PUBLIC
REF-ID:REF-RT-1003
Securing C2 Infrastructure for Red Team Operations Using Cloudflare Workers and Zero Trust Tunnels
A comprehensive guide to securing Command and Control infrastructure using Cloudflare Workers and Zero Trust Tunnels for Red Team operations.
Date: 2025-04-17
Read time: 15 mins
Author: 0xh3l1x
Command and ControlC2CloudflareOPSECRed TeamInfrastructure Security
red team
cat securing-c2-for-rt-operations.md

PUBLIC
REF-ID:REF-IOS-1001
iOS Pentesting Without Jailbreak v1: Obtaining and Testing iOS Apps
A comprehensive guide to downloading, decrypting, and pentesting iOS applications without requiring a jailbroken device
Date: 2025-04-10
Read time: 15 mins
Author: 0xh3l1x
iOSMobile SecurityPentestingAppleIPA
ios
cat ios-pentesting-v1-no-jb.md

PUBLIC
REF-ID:REF-MISC-1003
Virtualization on macOS: Running Intel Linux VMs on ARM
A comprehensive guide to running Intel-based Linux virtual machines on Apple Silicon Macs using custom virtualization solutions and OrbStack
Date: 2025-04-06
Read time: 15 mins
Author: 0xh3l1x
VirtualizationmacOSLinuxDevelopmentSecurity Research
misc
cat running-virtual-linux-intel-machines-on-macos-arm.md
PUBLIC
REF-ID:REF-REC-1003
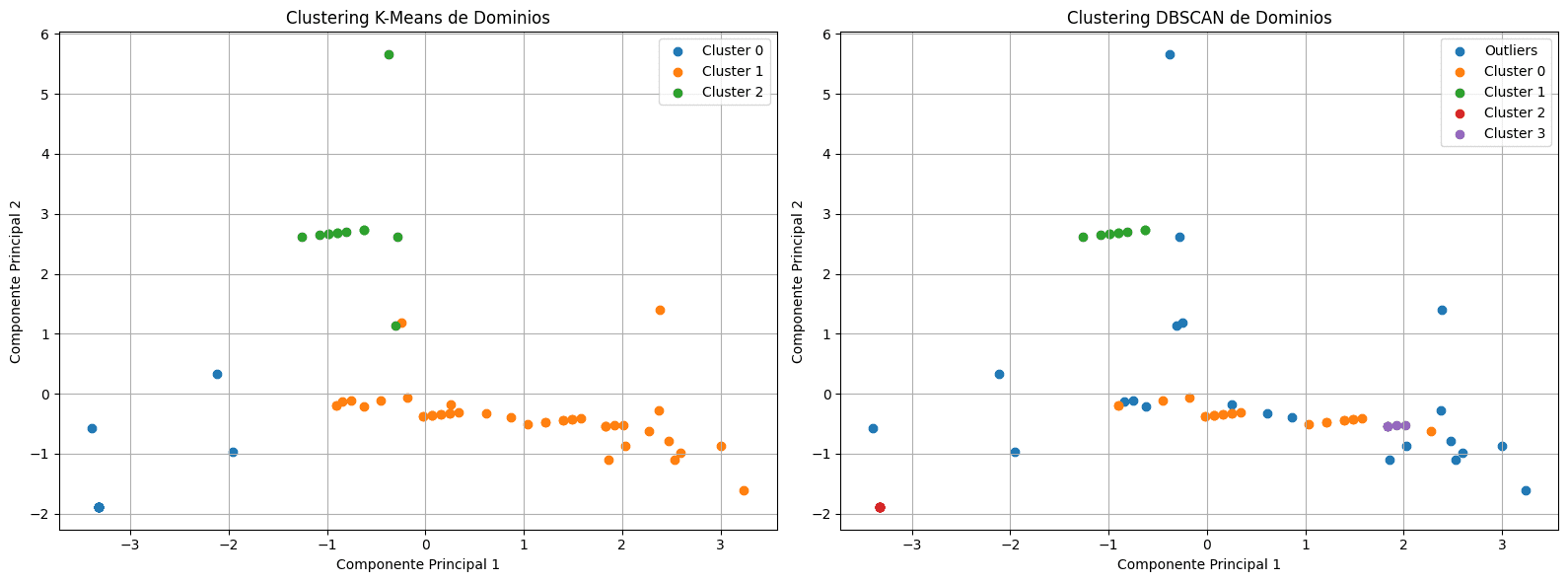
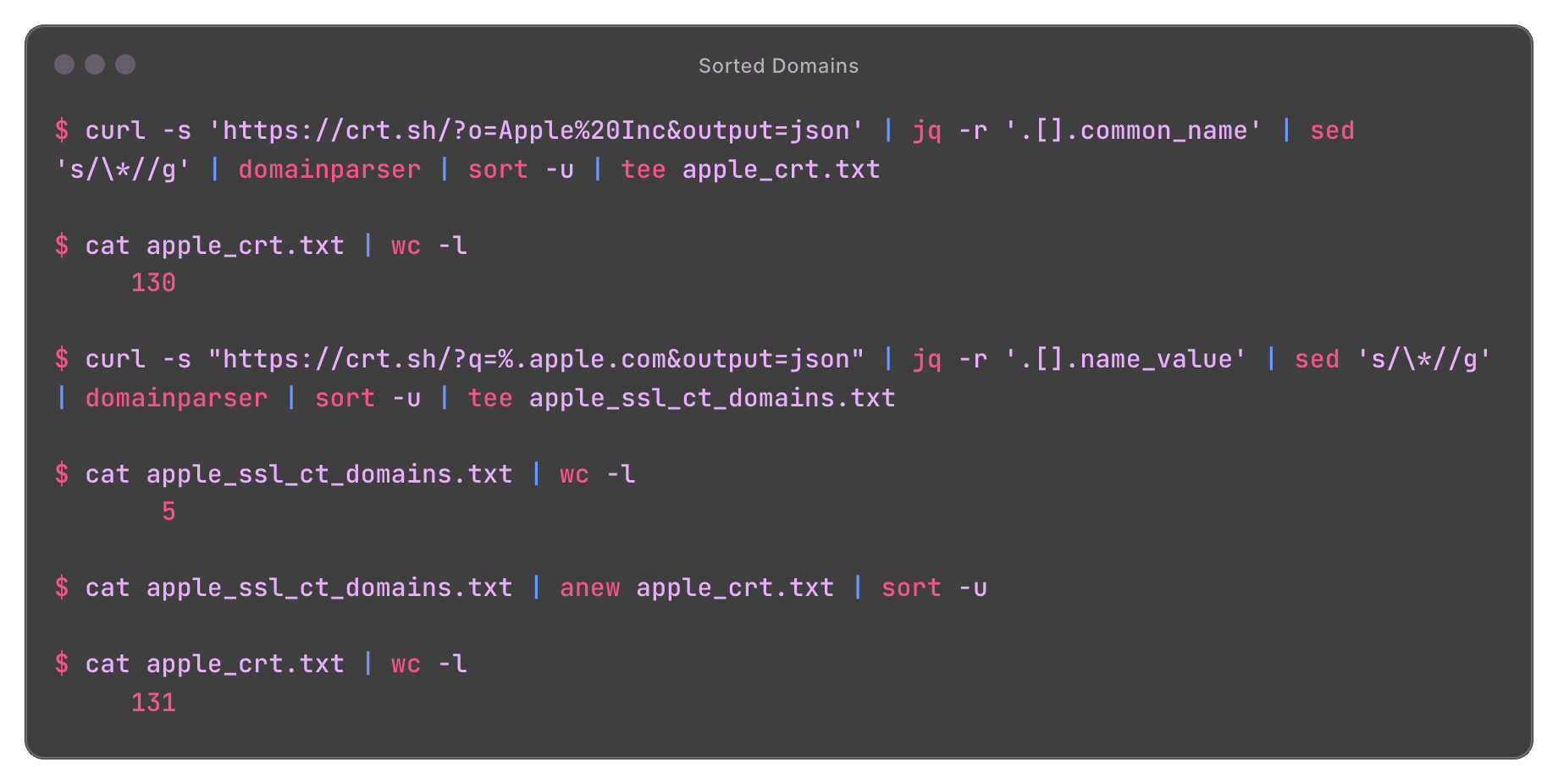
From 0 to Hero v2: The Startup Reconnaissance on Large Scopes
A comprehensive guide to conducting initial reconnaissance on large organizational scopes from scratch.
Date: 2025-03-20
Read time: 15 mins
Author: 0xh3l1x
ReconnaissanceBug BountyRed TeamSubdomain Enumeration
recon
cat from-0-to-hero-v2.md